Cybersecurity | Valley Tel Service
VTS delivers advanced cybersecurity services for businesses across the Pacific Northwest — offering real-time threat detection, compliance support, and 24/7 protection with SentinelOne’s AI-driven platform.
Cybersecurity Services to Protect Your Business in a Digital World
At VTS, our cybersecurity strategy is built around proactive protection, real-time monitoring, and rapid response. As a trusted Managed Services Provider (MSP), we deliver enterprise-grade cybersecurity solutions tailored to businesses of all sizes across the Pacific Northwest. From threat detection to compliance support, we help secure your digital assets so you can focus on growing your business with confidence.
Here’s a detailed overview of how we support our customers:
Proactive Threat Detection & Monitoring
We provide continuous, real-time surveillance of your entire IT ecosystem — including networks, servers, endpoints, and cloud systems — to detect early signs of threats, vulnerabilities, and unauthorized activities. By leveraging intelligent monitoring tools and behavior-based analysis, we can identify and contain potential issues before they escalate into serious incidents, minimizing downtime and protecting business operations.
Advanced Security Tools & Technologies
Our cybersecurity stack includes industry-leading technologies designed to combat today’s most dangerous cyber threats. This includes the deployment and management of firewalls, antivirus software, encryption protocols, and Security Information and Event Management (SIEM) systems. These tools work in concert to block malware, defend against phishing schemes, prevent ransomware attacks, and maintain the confidentiality and integrity of your sensitive business data.


Incident Response & Recovery
In the event of a cybersecurity incident, every second counts. Our team is prepared with rapid-response protocols to mitigate threats, contain breaches, and initiate remediation efforts. This includes isolating affected systems, recovering lost data, and restoring normal operations as quickly as possible. We prioritize minimizing business disruption and ensuring that your systems return to a secure, functional state without unnecessary delays.
Security Audits & Assessments
We regularly conduct comprehensive audits and security assessments to evaluate the effectiveness of your current security posture. These evaluations help identify vulnerabilities, outdated systems, or misconfigurations that may leave you exposed. Based on our findings, we provide actionable recommendations and implement enhancements to fortify your defenses and close any gaps in protection.
Compliance & Regulatory Support
Our services are designed to help you meet and maintain compliance with various industry standards and regulatory frameworks, such as GDPR, HIPAA, and PCI DSS. We guide you through the technical and procedural steps required to align with these standards — from data handling policies to reporting practices — ensuring that your business avoids costly penalties and operates with confidence in regulated environments.
Employee Training & Awareness
Your employees are often the first line of defense against cyber threats. That’s why we offer tailored training programs to educate staff on cybersecurity best practices, including how to recognize phishing attempts, use strong passwords, and follow secure protocols. This ongoing awareness training reduces the risk of human error and helps create a security-conscious workplace culture.
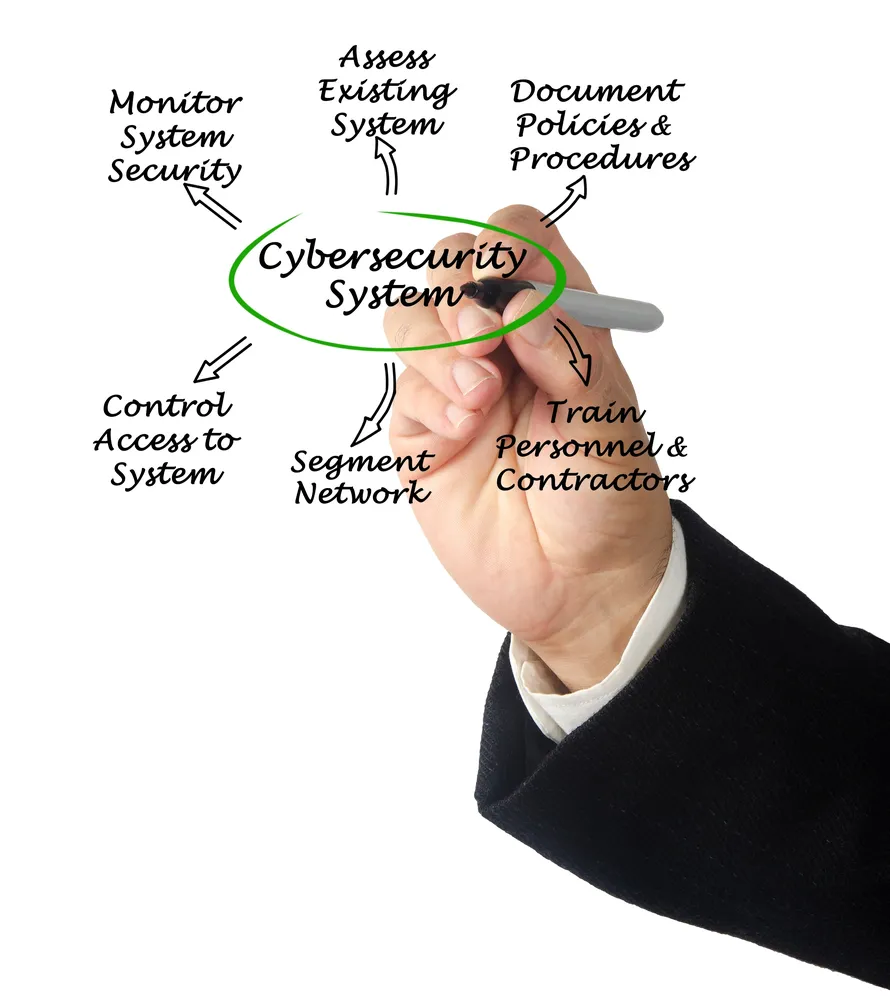
24/7 Support & Expertise
Cybersecurity threats don’t take time off — and neither do we. Our cybersecurity experts are available 24/7 to monitor systems, respond to threats, and offer expert guidance whenever needed. Whether it’s a late-night alert or an urgent compliance question, our team is ready to act quickly and decisively to protect your business around the clock.
Customizable Solutions
We understand that every business has unique cybersecurity requirements based on its size, industry, infrastructure, and risk exposure. That’s why we develop customized cybersecurity plans that align with your specific needs. From startups to enterprises, we provide scalable, flexible solutions that evolve with your business and keep pace with emerging threats.
Utilizing SentinelOne to Support Your IT Environment
Our cybersecurity offering is further strengthened by integrating SentinelOne, a cutting-edge, AI-driven endpoint protection platform. SentinelOne enables us to provide comprehensive, autonomous security that’s designed to prevent, detect, respond to, and remediate threats at machine speed. Here’s how SentinelOne supports and enhances your security strategy:
Endpoint Protection
Comprehensive Coverage: SentinelOne is deployed across all endpoint devices — including workstations, servers, laptops, and mobile devices — delivering robust protection across your digital environment. This real-time protection defends against malware, ransomware, zero-day exploits, and other advanced threats.
Behavioral AI: SentinelOne uses artificial intelligence to analyze behaviors, rather than relying solely on known signatures, which allows it to detect and block novel and emerging threats that traditional solutions may miss.
Threat Detection & Prevention
Real-Time Threat Detection: SentinelOne continuously monitors endpoint activities, identifying malicious behavior, anomalies, and suspicious interactions as they occur, allowing for instant containment and mitigation.
Automated Prevention: Once a threat is detected, SentinelOne responds automatically — blocking malicious actions, quarantining files, and preventing further spread — without needing human intervention.
Incident Response & Remediation
Automated Remediation: SentinelOne’s self-healing capabilities allow it to autonomously remove malware, restore damaged files, and isolate infected systems, significantly reducing the need for manual cleanup.
Deep Forensics: In-depth forensic tools enable detailed investigation of attacks, helping identify the root cause, attack vector, and impact. This insight helps refine future defenses and prepare for similar threats.
Centralized Management & Visibility
Single Pane of Glass: Through SentinelOne’s centralized console, we manage all endpoints across your organization from one dashboard. This allows us to maintain complete visibility into your endpoint security landscape and streamline operations.
Ransomware Protection
Ransomware Detection & Prevention: SentinelOne detects ransomware attacks at their earliest execution stages and halts them before data is encrypted, minimizing exposure and potential damage.
Rollback Capability: In the event that an attack succeeds, SentinelOne can automatically roll back files and systems to their pre-attack state, ensuring minimal data loss and business interruption.
Security Automation & Orchestration
Automated Workflows: SentinelOne integrates intelligent automation to handle routine incident response tasks, freeing up time and reducing the chance of human error.
Orchestrated Response: The platform connects seamlessly with other security tools to provide a synchronized, multi-layered response strategy that improves overall threat defense.
Advanced Threat Hunting & Intelligence
Threat Hunting: SentinelOne empowers us to conduct proactive searches for threats that may have bypassed automated detection systems, enabling us to stay ahead of adversaries.
Threat Intelligence: Its cloud-based threat intelligence feeds provide up-to-date insights into new attack methods, tools, and threat actors, helping us continuously refine and update your protection strategy.
Cloud-Native & Scalable Solution
Scalability: Built for the cloud, SentinelOne allows for easy scaling across multiple sites or growing businesses, without requiring additional infrastructure or overhead.
Cloud Integration: SentinelOne’s cloud-based architecture enables us to manage and secure endpoints from anywhere, simplifying deployment and reducing operational complexity.
Compliance & Reporting
Regulatory Compliance: SentinelOne helps fulfill audit and compliance obligations by maintaining detailed logs and event data, supporting frameworks like GDPR, HIPAA, and others.
Comprehensive Reporting: We provide detailed security reports that showcase threat activity, incident response timelines, system health, and user behavior to demonstrate proactive security efforts and maintain transparency.
24/7 Monitoring & Support
Managed Detection & Response (MDR): With our 24/7 MDR services layered on top of SentinelOne, we continuously analyze alerts, identify critical incidents, and take immediate action when necessary.
Proactive Incident Handling: SentinelOne’s automated remediation tools, combined with our expert oversight, ensure that threats are dealt with swiftly and effectively — often before you even know they existed.
By integrating SentinelOne, we offer an intelligent, scalable, and cost-effective way to protect your endpoints, reduce cybersecurity risk, and ensure compliance — all while giving your team peace of mind that your digital environment is secure.
Ready to Strengthen Your Security?
Contact us today to schedule a free cybersecurity consultation.






